When it comes to cloud services, many organizations seem to forget
their basic rules and responsibilities surrounding security. Some tend
to think because Microsoft hosts Office 365, for example, that Microsoft
will handle security for them. Unfortunately, they couldn’t be more
wrong.
Microsoft will protect your data from those who attempt to gain access to its systems, as well as offer protection from data loss due to an outage or failure of their infrastructure. However, if your credentials were to become compromised, you’re on your own as far as Microsoft is concerned. During the on-premises era, we were much more risk-conscious, and most companies had robust security policies in place. But now that data has become accessible from all over the world, it is crucial to be aware of the increase in risk and implement additional security measures to cover it.
In this article, we will share how you can improve your security within Office 365 without breaking the bank. If you have a full license of Office 365, these next five tips will be available for you to implement in your system today. If you are only paying for a subset of the services, like Exchange Online, your options will unfortunately be limited.
Login: Enable multi-factor authentication.
Most people are not good with passwords – period.

Fortunately,
Office 365 enables multi-factor authentication as a part of your Azure
Active Directory services. Users can define their preference of
multi-factor authentication options: they can use the multi-factor
authentication app, receive a phone call, or authenticate by text
message. Since your authentication process is a combination of something you know (username and password combination) and something you have (your phone), the risk of a malicious authentication getting through is slim.
For more information on multi-factor authentication in Office 365, check out this documentation.
Email: Block Client Rules Forwarding
To prevent content from leaving the organization by mistake, most people will refer to Data Loss Prevention (DLP). However, Office 365’s DLP requires an additional license or an upgrade of your existing license.
One simple way to avoid that investment but minimize the amount of information that travels outside of your organization’s walls is to limit or block email forwarding. Many people have multiple email addresses. Sometimes we see that people will set up client rules forwarding or redirect all email to their personal account, so they have one centralized mailbox. This practice is sure to give IT and security officers major heartburn, as it only increases an organization’s risk data breaches and leaks. This forwarding block is best achieved using a transport rule in Exchange Online:
Like it or not, phones have become the extension of our workplace. To make matters worse from a security perspective, these phones contain a lot of sensitive company data, and it’s usually a safe bet that our end-users haven’t taken the initiative to set up their phones as securely as possible.
For desktops and laptops, we tend to have a set of rules delivered through group policies or a similar process, but organizations tend to overlook the same need for security when it comes to mobile phones. Mobile Device Management (MDM) is natively enabled in Office 365. To set up MDM, you can go through the documentation here. With MDM you can define any number additional security measures with the ability to wipe a device remotely when needed. Why would you need to wipe a phone? Phones get stolen or lost all the time; the last thing you want is your corporate data to be available to anyone who ends up with that device next.
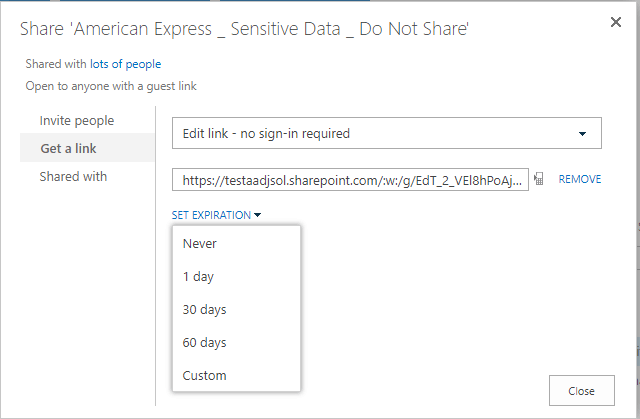
Documents: Configure expiration time for external sharing links. 
In a world where collaboration is the new norm, it should come as no surprise that people often use Office 365 share documents externally. There are many benefits to external sharing through Office 365: you are in control of the content, when a new version is delivered, its permissions, etc. However, when we share information, we tend not to question how long external links should be active. Is this sharing a one-time thing, or is it for long-term collaboration?
This becomes a security concern when we send out information where no sign-in is required. Since these questions should be answered on an organizational level as well as on an individual level, you’ll want to make sure there is at least an expiration time for anonymous links defined on an admin level. Unfortunately, there is no user interface for this setting (yet).
For now, you need to define this through PowerShell. You can use this script to set a default expiration timeframe of 30 days:
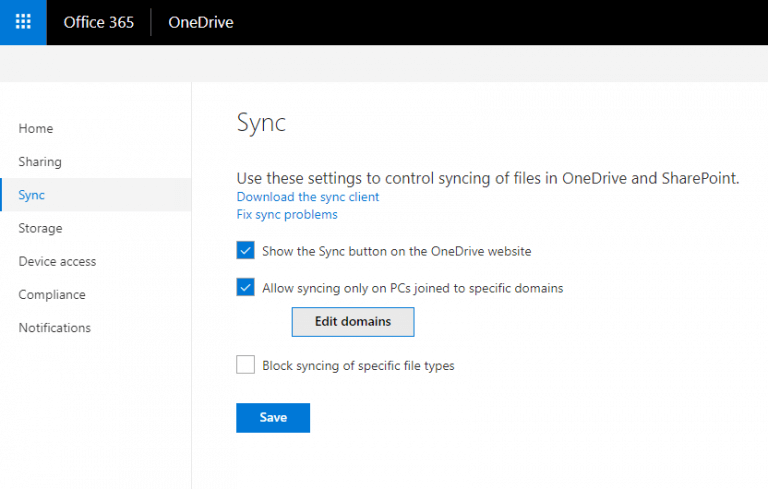

Sync only to domain-joined computers.
One of the most used features of SharePoint Online and OneDrive for Business is the sync functionality. It enables offline access to content, and most people like it because it functions similarly to a user drive. However, when you allow synchronization of content to computers that are not managed by your organization, you may be opening yourself up to serious data loss or a breach. We know that the security of home computers is in most cases insufficient for storing corporate data. Office 365 enables you to configure rules that only allow synchronization to domain-joined computers. People will still be able to use Office 365 from home PCs and laptops, but no data will sync to those computers. The setting for synchronization is found under OneDrive Admin (https://admin.onedrive.com) > Sync.
These are five simple things that your organization can do today to make your Office 365 environment more secure. Remember: Securing Office 365 is your responsibility, too. Microsoft is responsible for the things you cannot control like uptime, high availability, etc. But it’s important that you take the additional steps in-house to protect your mission-critical data.
Microsoft will protect your data from those who attempt to gain access to its systems, as well as offer protection from data loss due to an outage or failure of their infrastructure. However, if your credentials were to become compromised, you’re on your own as far as Microsoft is concerned. During the on-premises era, we were much more risk-conscious, and most companies had robust security policies in place. But now that data has become accessible from all over the world, it is crucial to be aware of the increase in risk and implement additional security measures to cover it.
In this article, we will share how you can improve your security within Office 365 without breaking the bank. If you have a full license of Office 365, these next five tips will be available for you to implement in your system today. If you are only paying for a subset of the services, like Exchange Online, your options will unfortunately be limited.
Login: Enable multi-factor authentication.
Most people are not good with passwords – period.

Password
For more information on multi-factor authentication in Office 365, check out this documentation.
Email: Block Client Rules Forwarding
To prevent content from leaving the organization by mistake, most people will refer to Data Loss Prevention (DLP). However, Office 365’s DLP requires an additional license or an upgrade of your existing license.
One simple way to avoid that investment but minimize the amount of information that travels outside of your organization’s walls is to limit or block email forwarding. Many people have multiple email addresses. Sometimes we see that people will set up client rules forwarding or redirect all email to their personal account, so they have one centralized mailbox. This practice is sure to give IT and security officers major heartburn, as it only increases an organization’s risk data breaches and leaks. This forwarding block is best achieved using a transport rule in Exchange Online:
IF The Sender is located ‘Inside the organization’Mobile: Enable mobile device management services.
AND IF The Recipient is located ‘Outside the organization’
AND IF The message type is ‘Auto-Forward’
THEN Reject the message with the explanation ‘External Email Forwarding via Client Rules is not permitted’.
Like it or not, phones have become the extension of our workplace. To make matters worse from a security perspective, these phones contain a lot of sensitive company data, and it’s usually a safe bet that our end-users haven’t taken the initiative to set up their phones as securely as possible.
For desktops and laptops, we tend to have a set of rules delivered through group policies or a similar process, but organizations tend to overlook the same need for security when it comes to mobile phones. Mobile Device Management (MDM) is natively enabled in Office 365. To set up MDM, you can go through the documentation here. With MDM you can define any number additional security measures with the ability to wipe a device remotely when needed. Why would you need to wipe a phone? Phones get stolen or lost all the time; the last thing you want is your corporate data to be available to anyone who ends up with that device next.

Documents

In a world where collaboration is the new norm, it should come as no surprise that people often use Office 365 share documents externally. There are many benefits to external sharing through Office 365: you are in control of the content, when a new version is delivered, its permissions, etc. However, when we share information, we tend not to question how long external links should be active. Is this sharing a one-time thing, or is it for long-term collaboration?
This becomes a security concern when we send out information where no sign-in is required. Since these questions should be answered on an organizational level as well as on an individual level, you’ll want to make sure there is at least an expiration time for anonymous links defined on an admin level. Unfortunately, there is no user interface for this setting (yet).
For now, you need to define this through PowerShell. You can use this script to set a default expiration timeframe of 30 days:
$tenantName = “yourTenantName”Of course, people will have the ability to override this date if they need to – but in the majority of cases, you will be covered by this default expiration timeframe.
$expirationinDays = 30
Connect-SPOService -Url “https://$($tenantName)-admin.sharepoint.com”
set-spotenant -RequireAnonymousLinksExpireInDays $expirationinDays

Sync

Sync only to domain-joined computers.
One of the most used features of SharePoint Online and OneDrive for Business is the sync functionality. It enables offline access to content, and most people like it because it functions similarly to a user drive. However, when you allow synchronization of content to computers that are not managed by your organization, you may be opening yourself up to serious data loss or a breach. We know that the security of home computers is in most cases insufficient for storing corporate data. Office 365 enables you to configure rules that only allow synchronization to domain-joined computers. People will still be able to use Office 365 from home PCs and laptops, but no data will sync to those computers. The setting for synchronization is found under OneDrive Admin (https://admin.onedrive.com) > Sync.
These are five simple things that your organization can do today to make your Office 365 environment more secure. Remember: Securing Office 365 is your responsibility, too. Microsoft is responsible for the things you cannot control like uptime, high availability, etc. But it’s important that you take the additional steps in-house to protect your mission-critical data.
Comments
Post a Comment